CYS4-SensitiveDiscoverer: finding secrets automatically during a PT
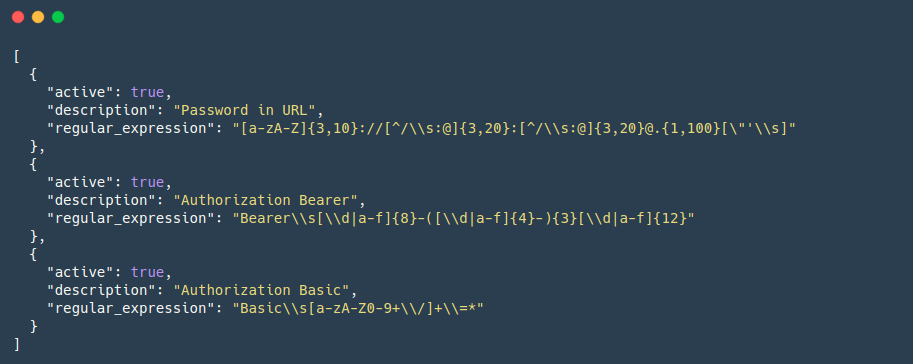
Table of contents
Introduction
Burp Suite is a software tool developed by a British company named Portswigger Ltd, used for web application security testing. It is an all-in-one set of tools used to perform penetration tests on web applications. The dozen tools that it incorporates help in the testing process: starting with mapping, analyzing the attack surface, and ending with the research and exploitation of vulnerabilities. Also, it is possible to improve his capabilities by installing add-ons. These add-ons are called BApps, and they can be installed directly from the BApp Store or installed manually. Burp Suite is the most popular tool among professional web application security testers, researchers, and bug bounty hunters.
While Burp Suite provides many functionalities already integrated, it does not offer the opportunity, and it does not have a fully customizable BApp that automatically scans a particular pattern or finds the presence of a file extension inside HTTP messages. Until now, Penetration Testers must do this work manually for every pattern or file extension.
During a Penetration Test activity, many HTTP requests and responses are generated, and the security personnel should inspect them manually to verify sensitive information. This manual process is very inefficient and expensive. Identifying potential sensitive information can be wasteful, tedious work, take enormous time without considering the human factor and the probability of errors. During our activities, we spend a lot of time analyzing every HTTP message to find some sensitive information. We strongly believe that security personnel should execute these analyses more efficiently with the help of automation. For this reason, we decided to develop an extension for Burp Suite to help Penetration Testers during the analysis of HTTP messages. A second reason, always linked to the previous one, which prompted us to develop this extension, is that it is possible to find a lot of sensitive information inside HTTP messages. As anticipated, it could be easy to forget to check and miss a critical disclosure during manual analysis.
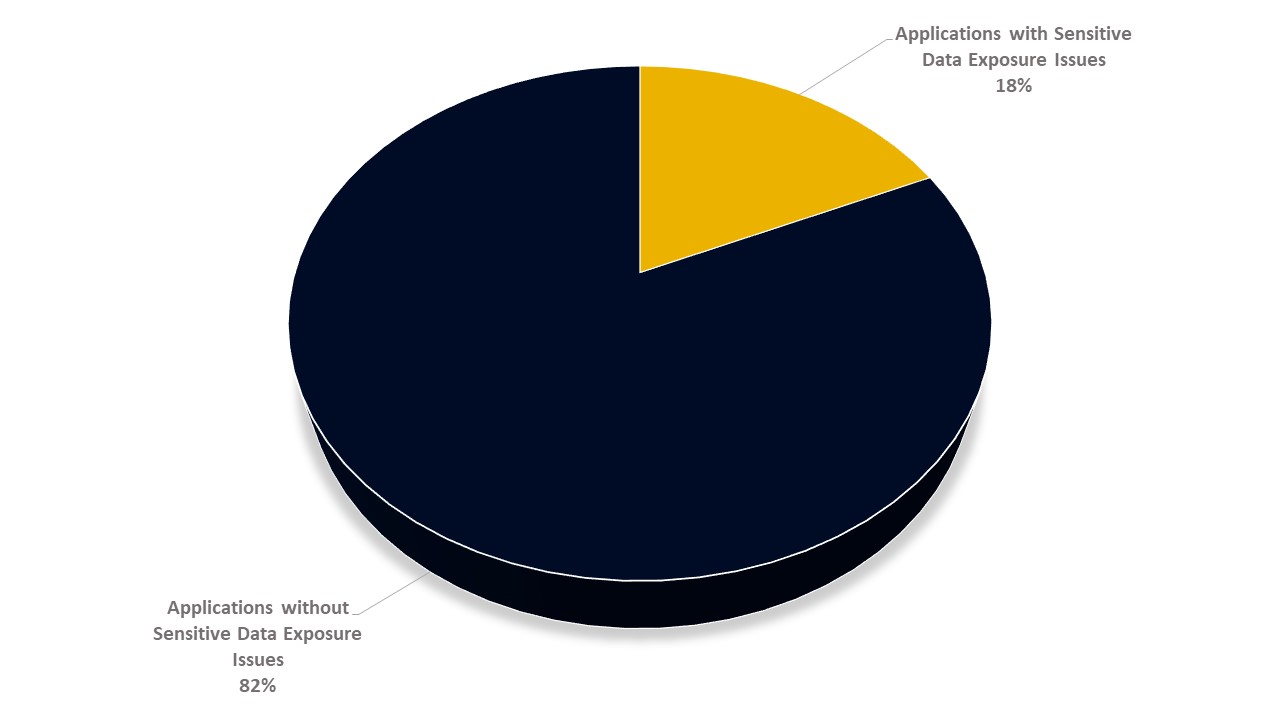
Over the past year, CYS4 has been able to identify different sensitive information present in HTTP messages, categorized as Sensitive Data Exposure. In terms of numbers, on our clients, this vulnerability is present 18% of the time. Given these results, it emerges that this vulnerability is present and constant within applications. Thanks to the BApp extension developed, we aim to improve these results and reduce the human-factor errors by improving the accuracy of our Penetration Test activities.
CYS4-SensitiveDiscoverer is a Burp Suite tool extension developed to automatically extract Sensitive Information from HTTP messages.
It checks for particular Regular Expressions or File Extensions inside HTTP response, and it will report every finding inside the UI. The plugin is available with a pre-defined set of Regular Expression and File Extension. Still, it is possible to choose which activate or deactivate and create your personalized lists.
How it works
CYS4-SensitiveDiscoverer is a Burp Suite extension that lets you scan the proxy history looking for potential Information disclosure. The main idea is that through specific regular expressions matched against the body and the headers of HTTP messages, you can find interesting data like passwords, API keys, client ids, ssh keys, and so on, automatically without manually inspect every message. In addition, it looks for particular file extensions by looking at the URLs.
We develop the tool to search sensitive information in an Offline mode. After you have interacted with a web application, you could start the extension that analyzes and scans the HTTP history of your project. This process is made in a separate thread so that you can continue to work with Burp. Once a regular expression or a file extension is matched against a message, a new row will appear in the extension UI tab. By selecting it, it is possible to see the corresponding Request and Response. It’s also possible to send the request to other Burp tools like Intruder or Repeater for further analysis.
Another advantage of CYS4-SensitiveDiscoverer is that you can manage the regular expressions or file extensions. The tool has a preset configuration for regexes and file extensions, but the Options panel lets you manage them. It’s possible to manage and adapt the lists as needed of the penetration tester: for every list, you can activate or deactivate an entry and create or delete an entry as you prefer.
Preparation phase
The first thing to look at is the in-scope filters, as the name suggests, which makes the extension analyze only in-scope requests. This filter could exclude many entries and save time without looking for out-of-scope matches. The other options are regarding the Regex List and Extension List. You can interact with the lists in the same manner. Each table has the following settings:
- Active: this checkbox is present for every entry. If selected, the analyzer will include the relative entry in the process of scanning.
- Reset: this button will reset the list to the predefined set of it.
- New: this button will add a new entry (a popup menu will appear, and you have to insert the expression and a brief description of it).
- Delete: this button will delete the selected entry.
- Clear: this button will clear the list by deleting all the entries.
- Open: this button will load a list of regular expressions/file extensions from a file; CYS4-SensitiveDiscoverer can handle txt or csv file in which the data are in the following format:
- Regex
^[\"|'].*[\"|'],(\\s)?[\"|'].+[\"|']$ - File extension
^[\"|'].*[\"|'],(\\s)?[\"|'](^)?\\..+[\"|']$
Those expressions mean that every line in the file you want to load has to be in the following form:
“description",“expression”;You are free to use single quotes or double quotes, and the description can be empty; the expression for file extension must start with a dot.
- Regex
- Save: this button will save the actual list for further analysis.
Once you have your favorite list of regexes and extensions set up, you can start the analysis in the Logger panel.
Presentation Phase
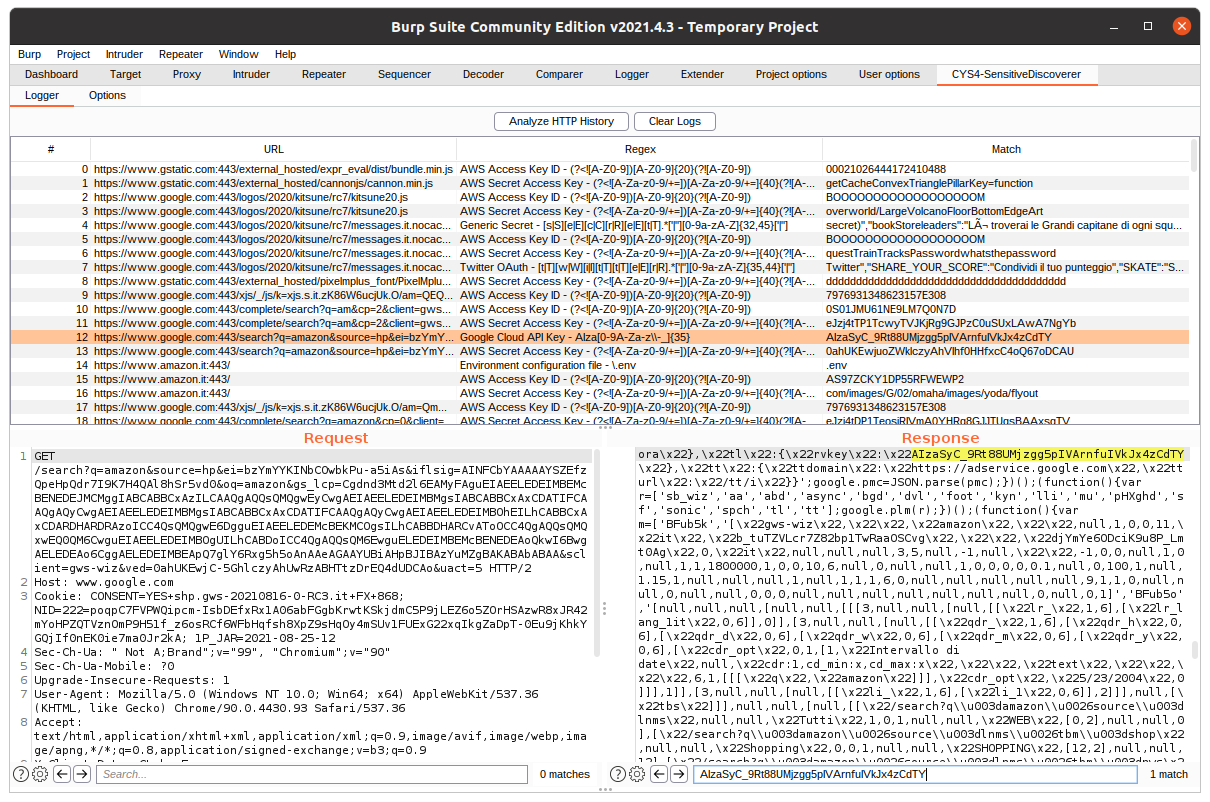
Penetration testers can start the automated analysis by clicking Analyze HTTP History inside the main panel. This button will start the analysis, and, in case of matches, the UI begins to populate. Every entry will have the corresponding URL of the matched request, the regex matched, and which string has matched from the HTTP messages.
By selecting one entry, penetration testers can see in the two panels under the logger the request and the response; the search bar in the response panel is populated with the matched string, so it will be easy to identify it with all the possible occurrences. Right-clicking an entry, you can send the request to other Burp tools or remove it.
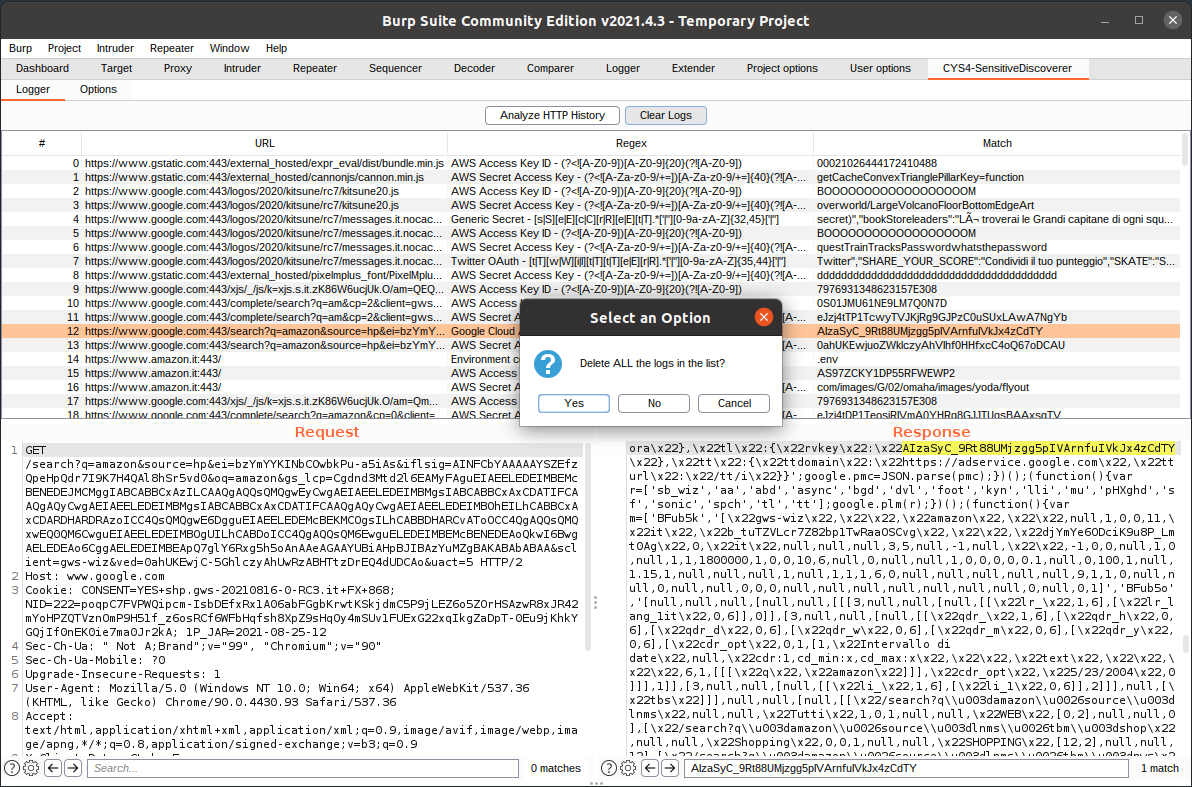
Once the analysis is completed, the penetration tester could exclude false positives by tuning the lists in the Option panel, clearing the Logger panel by clicking the Clear Logs button, and restarting the analysis process. This scan will probably take less amount of time if you exclude some entry from the process. It’s possible to repeat this process any time you want until you eliminate all the entries you don’t want to log.
Next steps
CYS4-SensitiveDiscoverer will continue to get updated, and we will improve the pre-set options during the time.
We are also planning to add new functionalities like the following:
- Entropy Analysis: the idea is to find the specific high entropy content that could refer to a possible sensitive content like RSA keys.